Install and configure #Windows Server 2012 R2 IP Address Management (IPAM)
Link Here
Strong and 2-Factor Authentication Headaches!
Tuesday 4 February 2014
Windows XP End of Life - What does this mean to you and your business?
On April 8, 2014, support and updates for Windows XP will no longer be available.
So what does this mean?
After April 8, 2014, technical assistance for Windows XP will no longer be available, including automatic updates that help protect your PC. Microsoft will also stop providing Microsoft Security Essentials for download on Windows XP on this date. (If you already have Microsoft Security Essentials installed, you will continue to receive anti-malware signature updates for a limited time, but this does not mean that your PC will be secure because Microsoft will no longer be providing security updates to protect your PC.)
The Risk?
If you continue to use Windows XP after support ends, your computer will still work but it might become more vulnerable to security risks and viruses
What to do?
You and your company need to license for and upgrade to Windows 7 or Windows 8.1 to ensure that your environment is fully supported by Microsoft moving forwards.
Monday 3 February 2014
Microsoft Windows, Cloud and Remote Access Blog
Challenge
Many companies allow remote access to their internal critical applications for both their staff and partners. This is great as it increases productivity for your business and allows your staff to work more flexibly. So prior to providing remote access, hopefully your remote access solution has been designed securely?
So what if it has, does this make access to your internal applications secure? The short answer is maybe but can it be made more secure? Of course.
Solution
One way of providing an extra layer of security for remote access is through enforcing 2-factor authentication. This simply means authenticating users must use two methods before being allowed access to their required applications and services. The most common authentication methods are:
User Name and Password Authentication - Active Directory (AD) authentication
2nd Factor of authentication - One Time Code (OTC).
So what is an OTC? There are different ways of receiving an OTC. One example is when a user is assigned a PIN number and from this PIN they can decipher their OTC. Some examples are posted here
Options for 2nd-Factor
The second factor can be true 2nd factor or it could be strong authentication. So what is the difference here? True 2-Factor authentication - This is where you receive your 2nd factor via a separate delivery method. This could be a physical token, email or SMS. The later two methods are classed as tokenless means of obtaining your OTC.
Strong Authentication - This is where you are presented with an option to obtain your OTC through a visual display on your screen. Example of Strong Authentication.
Above you can see that the mechanism to obtain your OTC is on the screen. Not the most secure method as somebody who knows your PIN and user credentials can work out your OTC and impersonate you. But this method is still more secure that just providing a username and password.
Takeaway
There are many vendors providing 2-factor solutions. However the majority of vendors only offer a physical token option. However a company in the UK, Swivel Secure, provide a token and tokenless authentication solution for the end user.
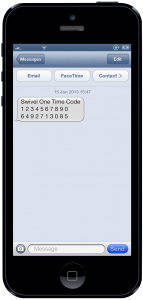
So how does the user receive their OTC to be able to authenticate. This is achieved by receiving their PIN either through SMS or Email. So as long as they have their laptop or smartphone with them they can receive their OTC. Example of tokenless 2-Factor authentication:
Above you can see how the user received their OTC via their mobile phone. Who doesn't carry a smartphone around these days? Not many people. However if a user does not have a smartphone then they simply get assigned the email OTC transport method.
Finally...
So what applications support 2-Factor? Well there are a number of platform that support 2-factor. These include:
and many more.....
Many companies allow remote access to their internal critical applications for both their staff and partners. This is great as it increases productivity for your business and allows your staff to work more flexibly. So prior to providing remote access, hopefully your remote access solution has been designed securely?
So what if it has, does this make access to your internal applications secure? The short answer is maybe but can it be made more secure? Of course.
Solution
One way of providing an extra layer of security for remote access is through enforcing 2-factor authentication. This simply means authenticating users must use two methods before being allowed access to their required applications and services. The most common authentication methods are:
User Name and Password Authentication - Active Directory (AD) authentication
2nd Factor of authentication - One Time Code (OTC).
So what is an OTC? There are different ways of receiving an OTC. One example is when a user is assigned a PIN number and from this PIN they can decipher their OTC. Some examples are posted here
Options for 2nd-Factor
The second factor can be true 2nd factor or it could be strong authentication. So what is the difference here? True 2-Factor authentication - This is where you receive your 2nd factor via a separate delivery method. This could be a physical token, email or SMS. The later two methods are classed as tokenless means of obtaining your OTC.
Strong Authentication - This is where you are presented with an option to obtain your OTC through a visual display on your screen. Example of Strong Authentication.
Above you can see that the mechanism to obtain your OTC is on the screen. Not the most secure method as somebody who knows your PIN and user credentials can work out your OTC and impersonate you. But this method is still more secure that just providing a username and password.
Takeaway
There are many vendors providing 2-factor solutions. However the majority of vendors only offer a physical token option. However a company in the UK, Swivel Secure, provide a token and tokenless authentication solution for the end user.
So how does the user receive their OTC to be able to authenticate. This is achieved by receiving their PIN either through SMS or Email. So as long as they have their laptop or smartphone with them they can receive their OTC. Example of tokenless 2-Factor authentication:
Above you can see how the user received their OTC via their mobile phone. Who doesn't carry a smartphone around these days? Not many people. However if a user does not have a smartphone then they simply get assigned the email OTC transport method.
Finally...
So what applications support 2-Factor? Well there are a number of platform that support 2-factor. These include:
- Office 365
- Microsoft Unified Access Gateway
- Mcrosoft SharePoint
- Mixrosoft Exchange Outlook Web App
- Citrix CAG
- Firewalls (Cisco, Checkpoint, Juniper...)
- IPAD Citrix Receiver
- Microsoft AD FS
- Microsoft IIS
- VMWare View
- F5
and many more.....
Subscribe to:
Posts (Atom)